Networking in AWS
Networking is one of the core pillars of the cloud computing model. Amazon VPC(virtual private cloud) helps you launch a secure, isolated private cloud hosted within a public cloud.
In a multi-account environment, you must find a way to create VPCs and associated objects across managed accounts. AWS recommends creating a Network account under the Infrastructure OU.
AWS SRA Infrastructure OU - Network Account
AWS Security Reference Architecture states that the Network account is the gateway between your apps and the Internet. Network resources are defined at one account, and then, leveraging another managed service called RAM(Resource Access Manager), these resources can be shared with accounts in the organization or only with the accounts within one or more specified organizational units (OUs).
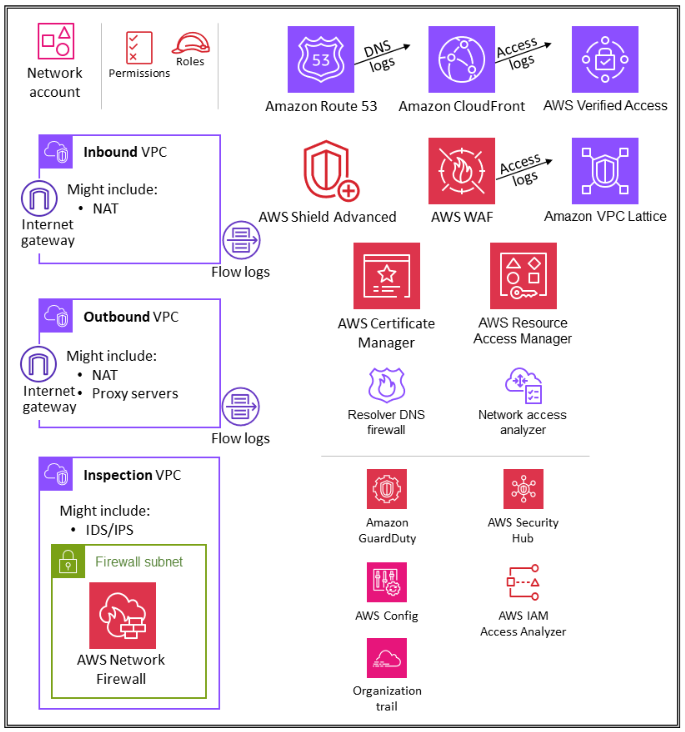
Figure1: AWS Security Reference Architecture
GitHub Repository
The source code can be found HERE
Building the Connectivity
In one of the blogs, I talk about setting up an AWS landing zone using the control tower.
Followed these steps from the control tower section of the Management account
- Create an OU named
Infrastructure
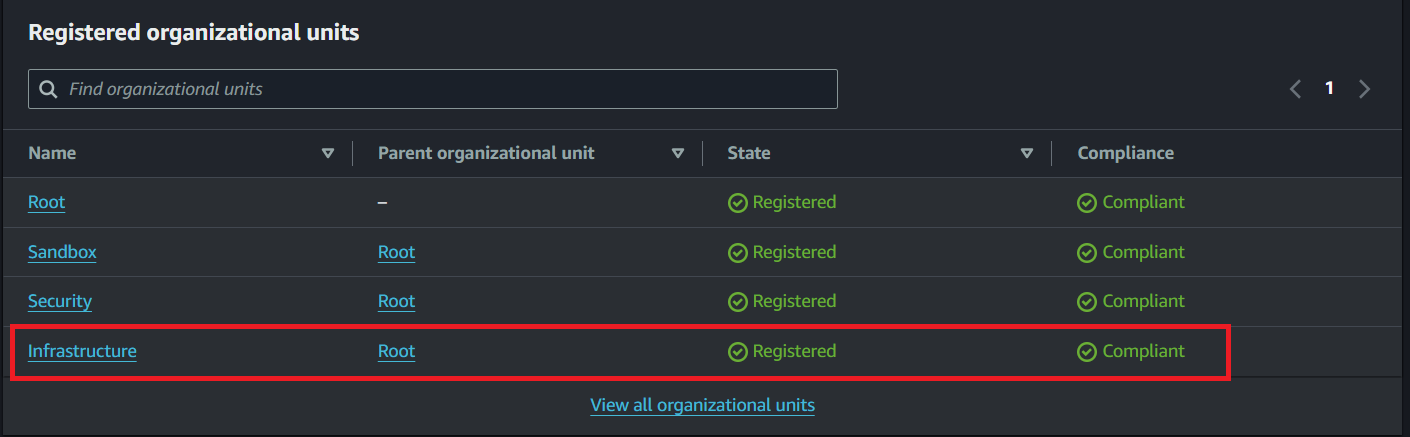
Figure2: Infrastructure-OU
- Create an AWS account named
Networkfrom the account factory.
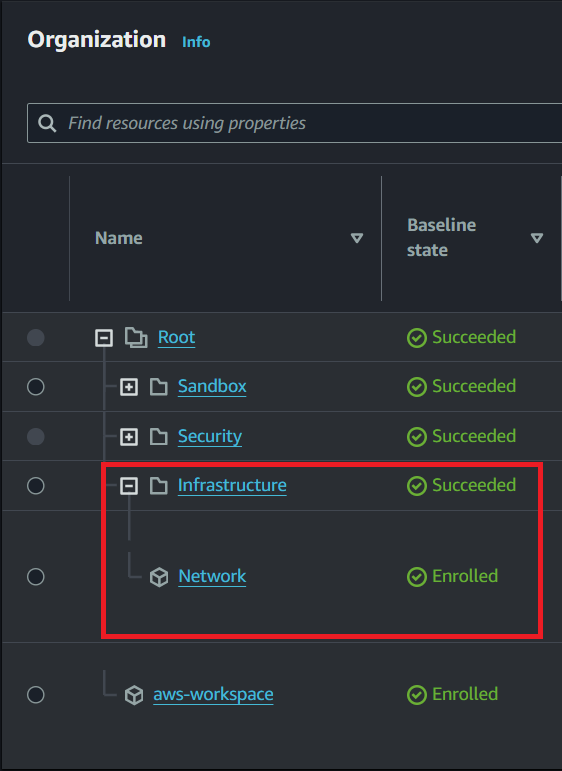
Figure3: Network Account
- Disable automatic creation of VPCs in all regions by the Account Factory in AWS Control Tower.
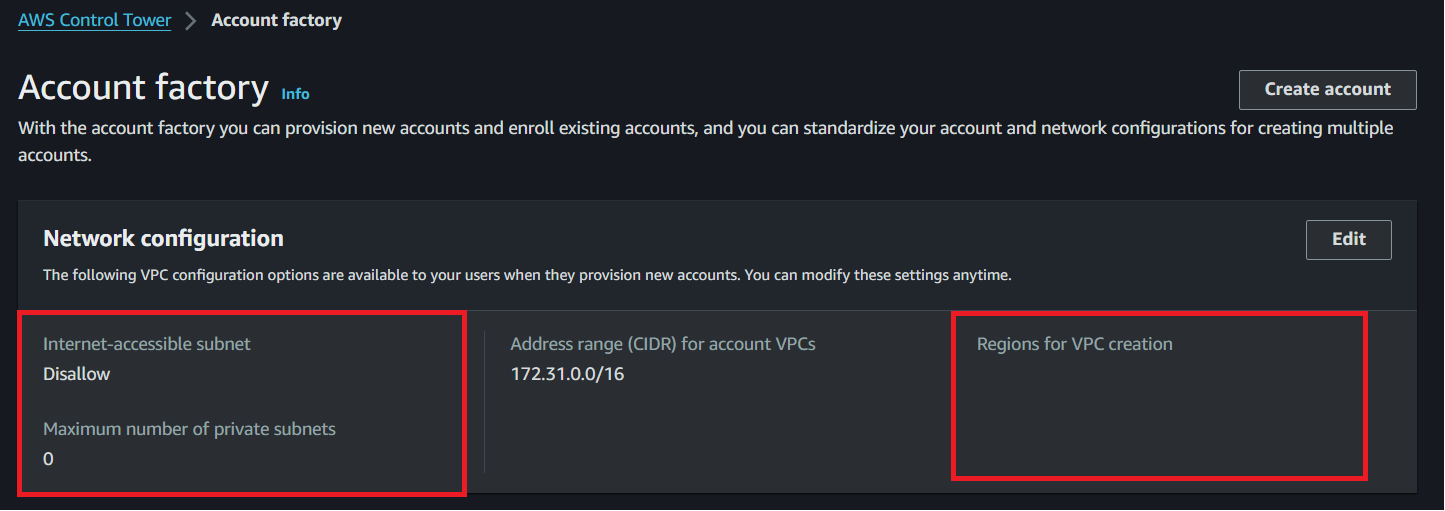
Figure4: Network Configuration
In another post, I discussed the steps to integrate GitHub with AWS using OIDC. In the same way, HCP Terraform must also be integrated with AWS for infrastructure provisioning. Add HCP as the OIDC provider on the AWS and create an IAM role. This role must be added as a variable on your HCP workspace/organization.
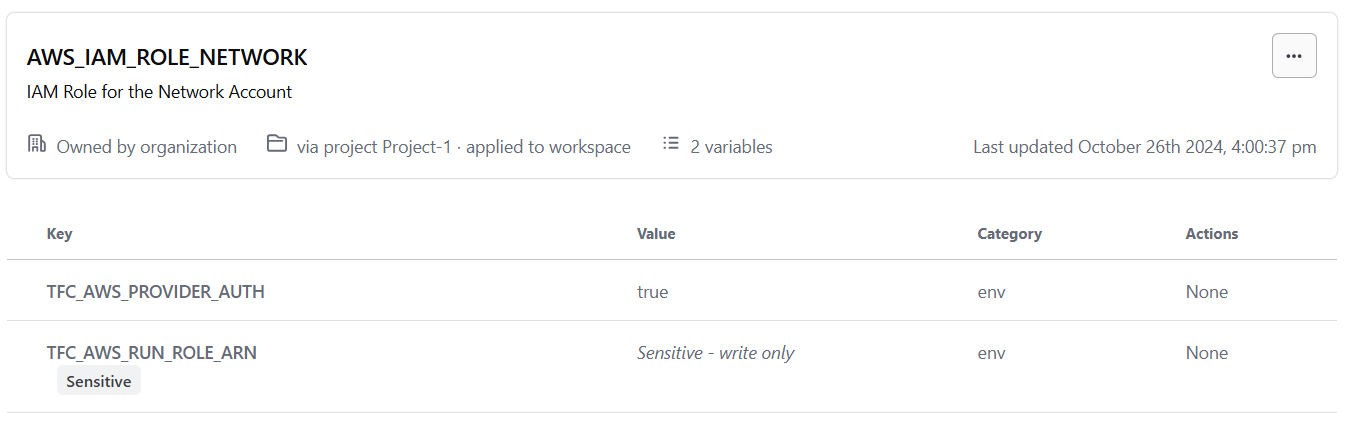
Figure5: HCP Variables
Virtual Private Cloud(VPC)
Our new VPC contains the following resources:
- Two public subnets
- Two private subnets
- One internet gateway
- Four routing tables
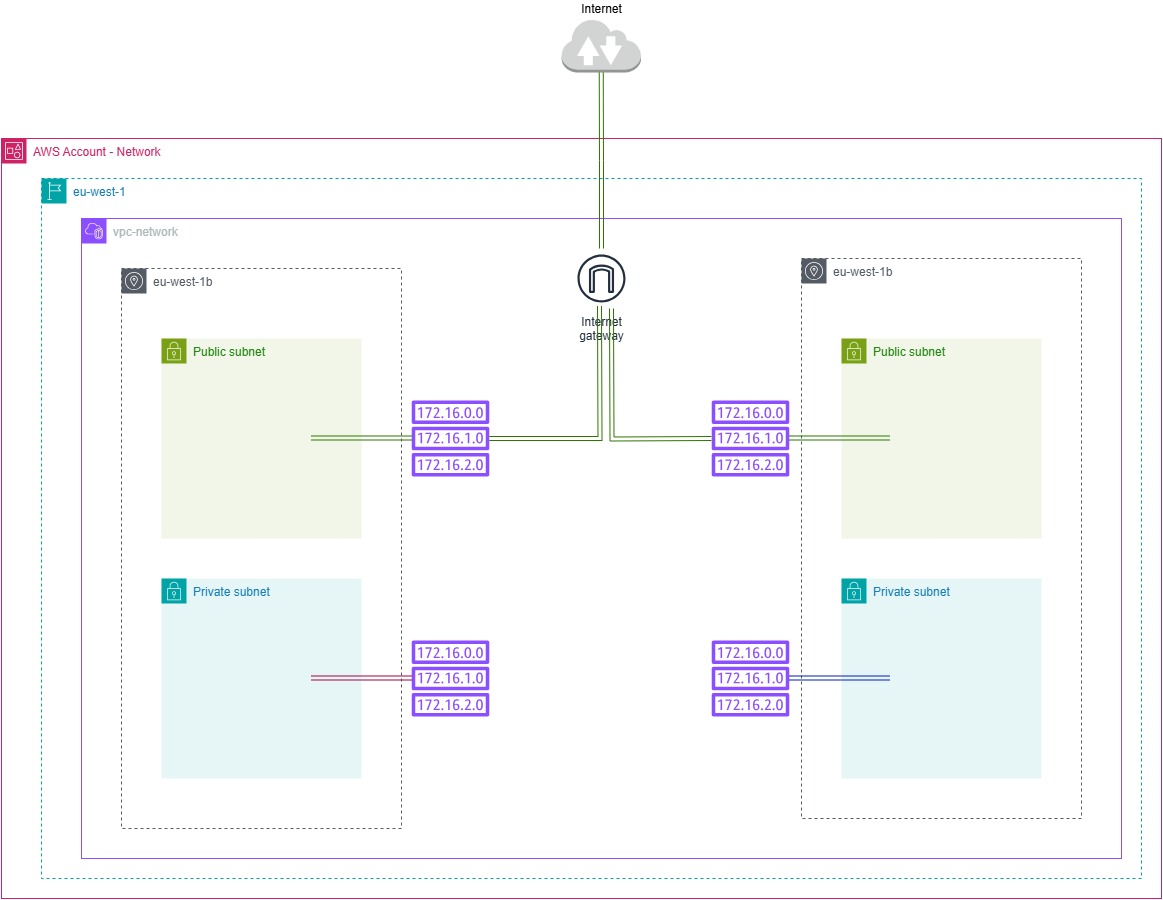
Figure6: VPC Overview
A successful workflow summary will look like this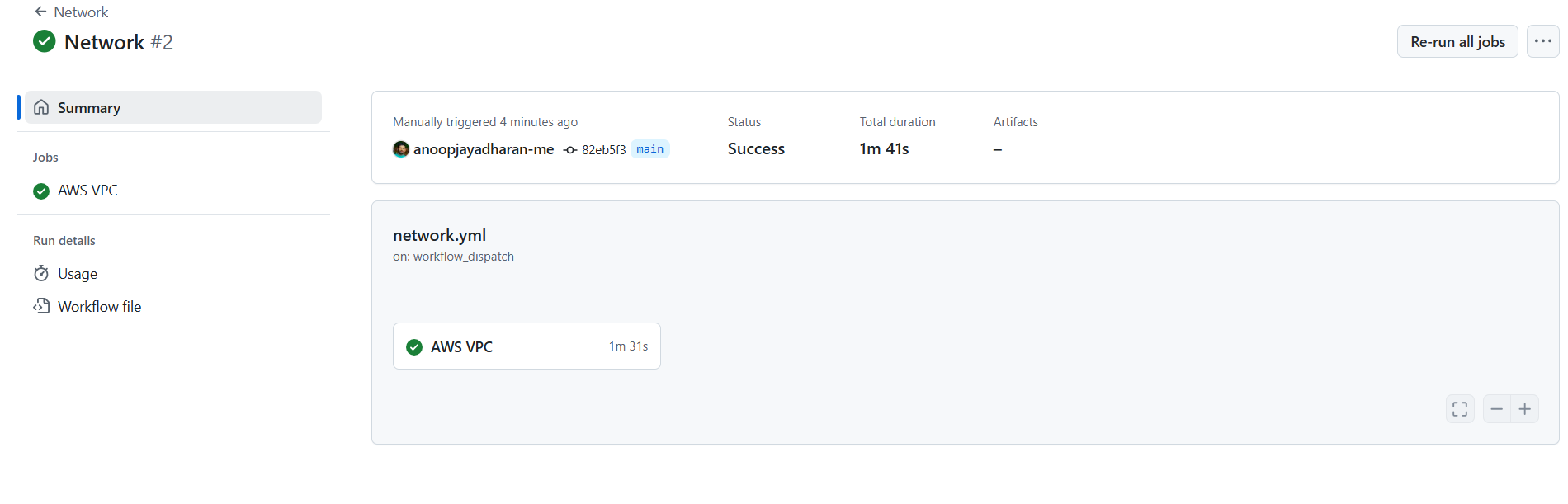
Figure7: Workflow Summary
Network Account
Connect to the Network account and verify the VPC creation.
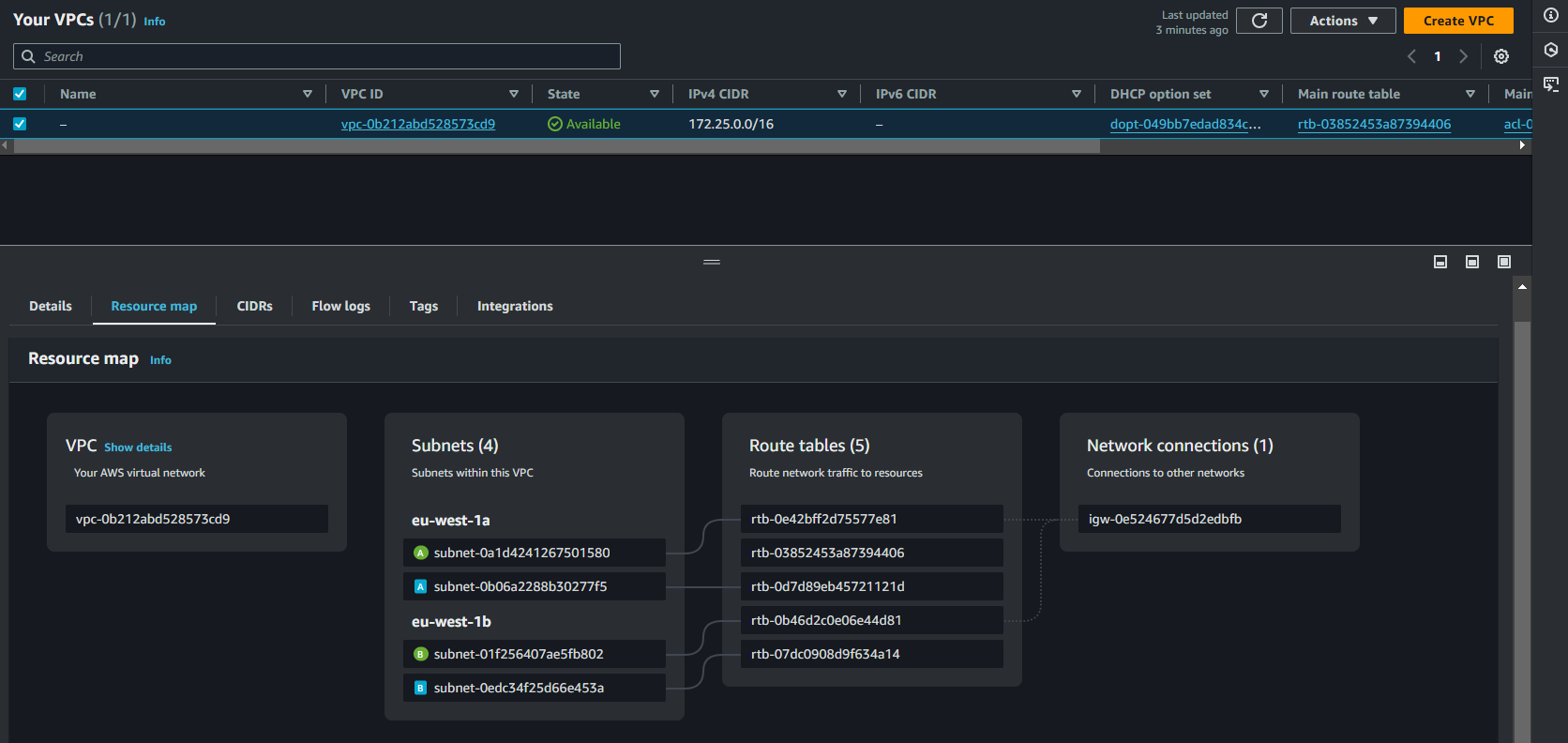
Figure8: VPC Resources
Resource Access Manager(RAM)
The last step is to create a resource share using AWS Resource Access Manager(RAM) to share all four VPC subnets with the “Sandbox” OU.Figure9: Resource Access Manager
ram.tf as follows | |
One quick tip is to add the ARN of Sandbox OU to the Terraform workspace.
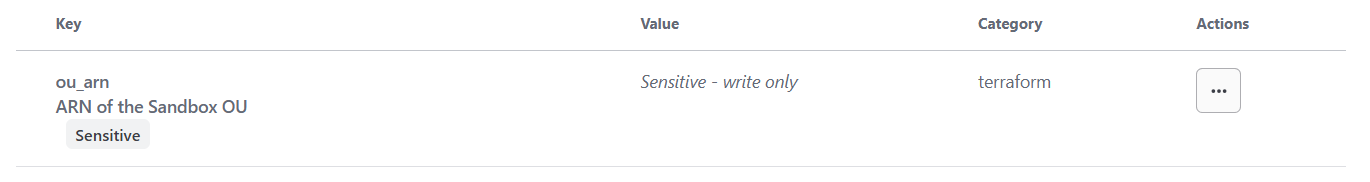
Figure10: Workspace Variable
Resource share has been created and will look like the one below. Notice “shared by me”, ie, the Network Account
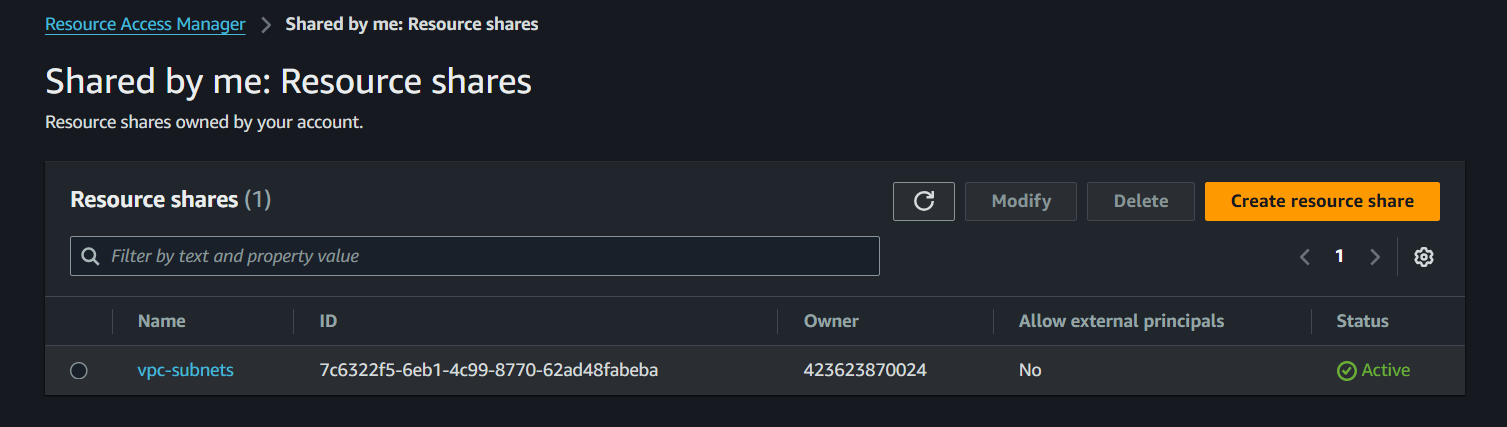
Figure11: Resource Share-by me
Development Account
Connect to the “development” account, and you will see “shared with me” under RAM.
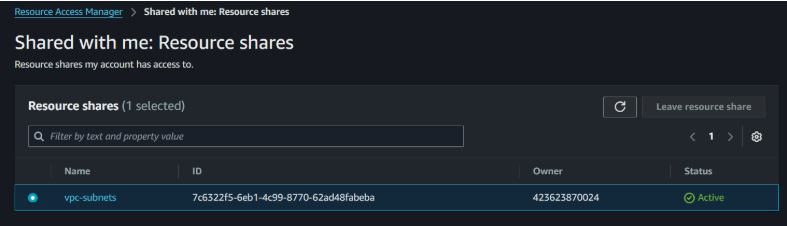
Figure12: Resource Shared-with me
In this way, all future accounts within Sandbox OU will inherit the shared VPC from the Network account.
