AWS Landing Zone using Control Tower
Companies that follow the AWS Security Reference Architecture will have multiple accounts for various teams or divisions. As a Cloud/DevOps engineer, you are responsible for managing those accounts.
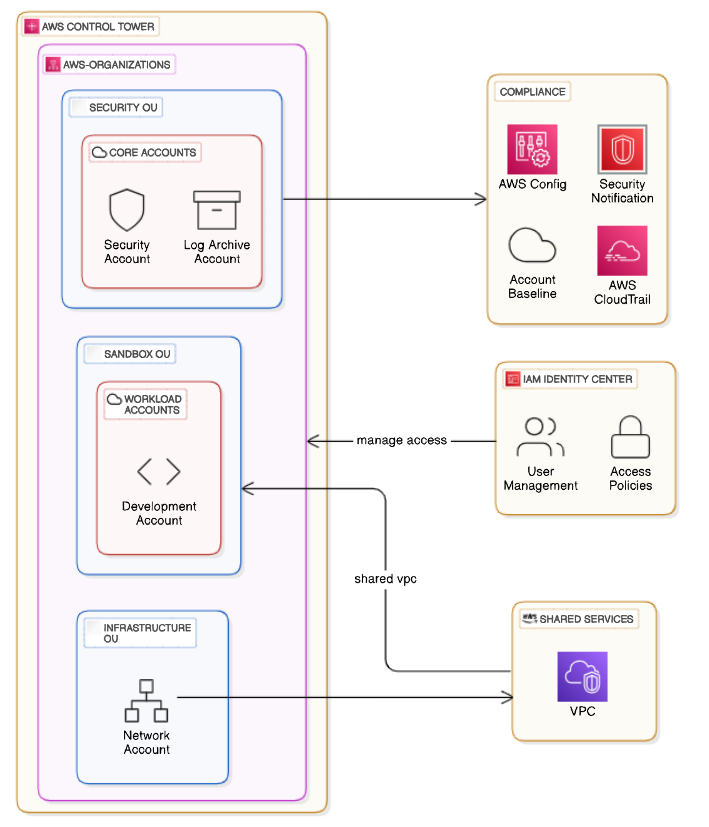
Figure1: Landing zone Overview
Landing Zone
Recently, I set up a landing zone on AWS using the control tower. A landing zone is a well-architected, multi-account, scalable, and secure AWS environment. It is a starting point from which your organization can quickly launch and deploy workloads and applications confidently in your security and infrastructure environment.
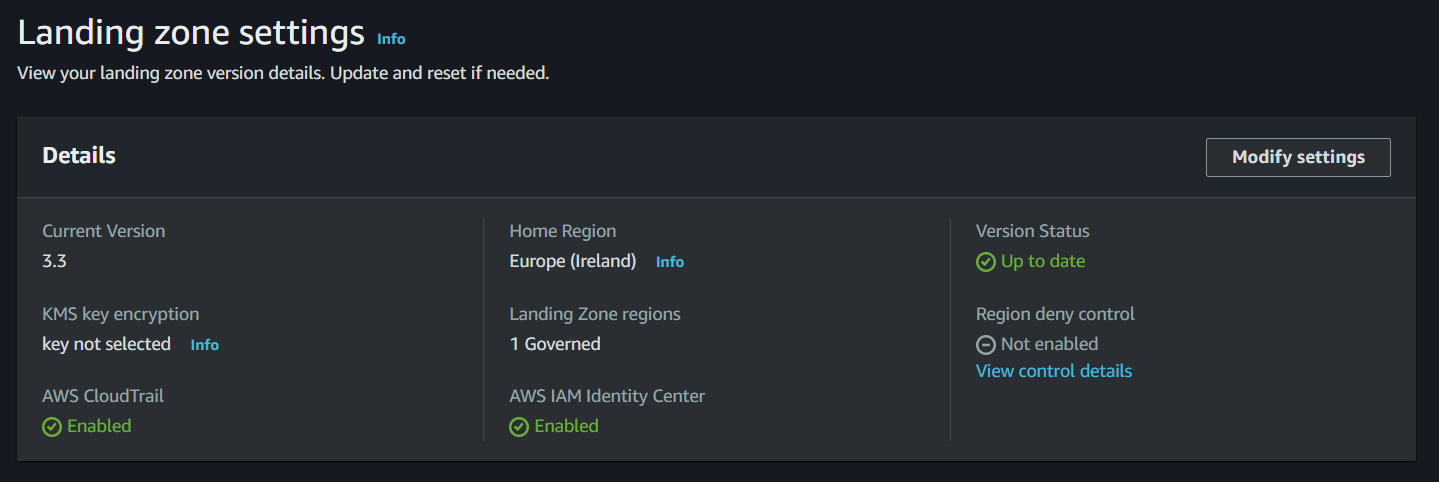
Figure2: Settings
Control Tower
AWS Control Tower automates the setup of a new landing zone by using best practices, blueprints for identity, federated access, and account structure. Some of the blueprints implemented on AWS Control Tower include:
- A multi-account environment using AWS Organizations
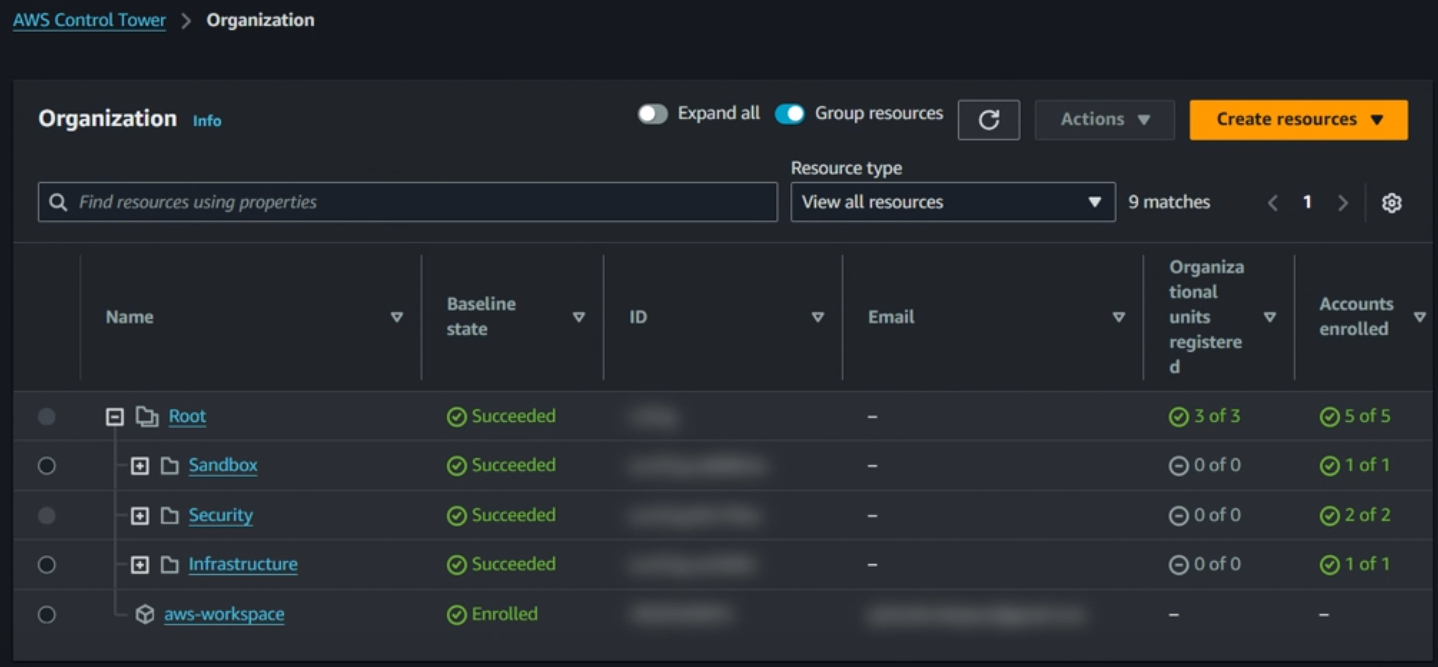
Figure3: AWS Organization
Cross-account security audits using AWS Identity and Access Management (IAM) and AWS IAM Identity Center
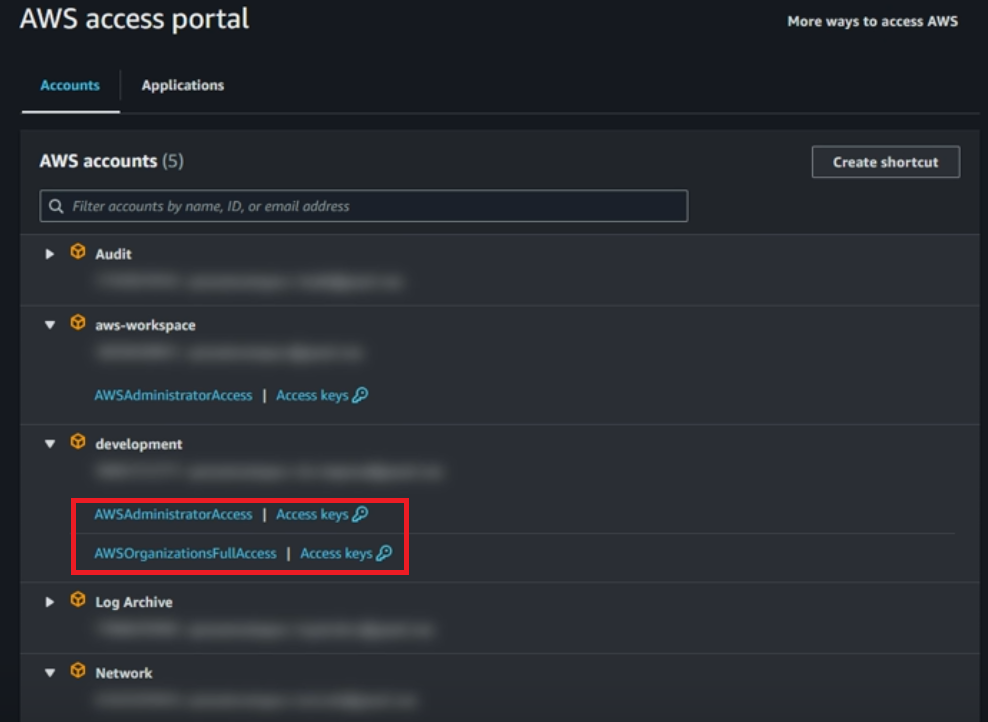
Figure4: User Access Portal
Identity management using the Identity Center default directory
Centralized logging from AWS CloudTrail and AWS Config stored in Amazon Simple Storage Service (Amazon S3)
In addition, an IAM user with admin privilege is created on the IAM Identity Center to manage user access to AWS accounts centrally.
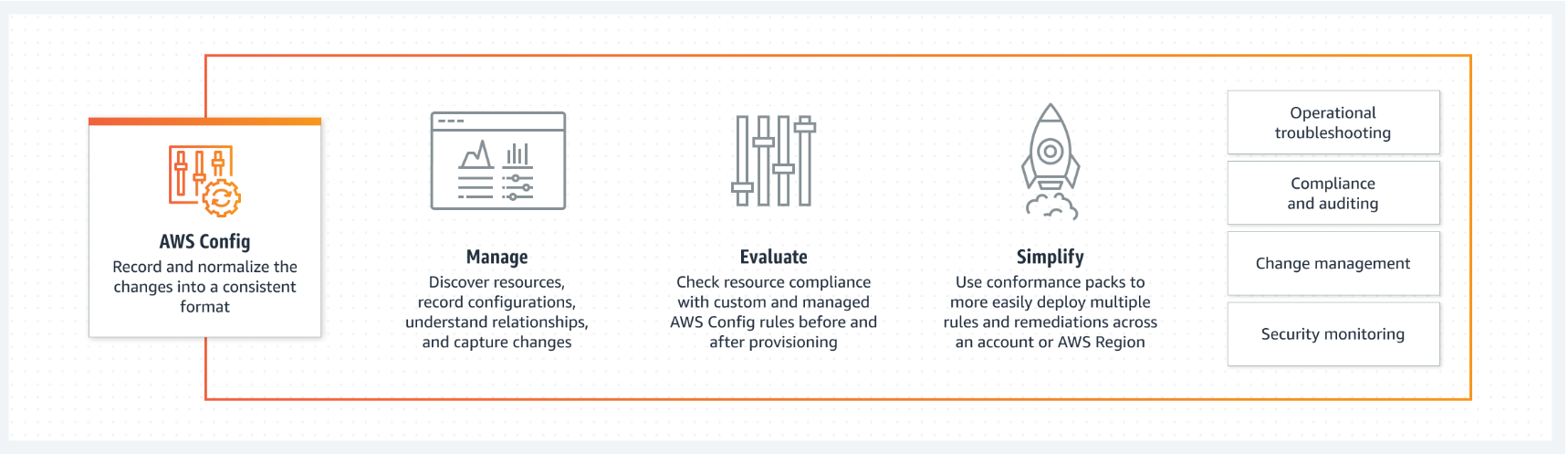
AWS Config
AWS Config provides a detailed view of the configuration of AWS resources in your AWS account. This includes how the resources are related to one another and how they were configured in the past so that you can see how the configurations and relationships change over time.Figure5: AWS Config